Guarding Health Data and Ensuring Peace of Mind – Your Compliance, Our Commitment
As healthcare technology risks evolve, so do the complexities of regulatory compliance and cybersecurity threats. At PBMares, we understand that the intersection of healthcare and technology demands a specialized approach to risk management. Our suite of services, including HIPAA risk assessments, SOC 2 + HIPAA report integration, and HITRUST readiness assessments (encompassing either the e1, i1, or r2 frameworks), ensure that your organization is compliant and fortified against emerging risks.
HIPAA Risk Assessments: Protect Patient Data with Precision
Both healthcare organizations and companies that, during the normal course of business, receive and process protected healthcare information are the custodians of highly sensitive patient information. To navigate this immense responsibility and the regulations and fines associated with non-compliance, a comprehensive HIPAA risk assessment is indispensable. Our team of experts will:
- Perform a data mapping of in-scope systems and locations where electronic protected health information (ePHI) is stored or could be stored.
- Conduct thorough evaluations of potential vulnerabilities within your systems.
- Assess the security measures currently implemented against the HIPAA Security Rule.
- Provide detailed recommendations to manage and mitigate risks effectively.
You’ll receive clear, actionable recommendations to enhance your data protection strategies, ensuring compliance with the stringent regulatory standards of HIPAA. We don’t just highlight the risks; we partner with you to forge a robust defense against threats, keeping patient trust at the core of our mission.
SOC 2 + HIPAA: The Synthesis of Security Standards
Aligning SOC 2 principles with HIPAA requirements is more than a checkpoint—it’s a proactive step toward reinforcing trust in your healthcare services. Our SOC 2 + HIPAA integration services represent a unified approach to compliance, merging the rigorous standards of SOC 2 with the specialized requirements of HIPAA. This unique blend ensures that organizations that process ePHI meet the baseline criteria of HIPAA and exceed expectations with the robust controls and processes associated with SOC 2 reports.
With a SOC 2 + HIPAA integrated approach, you receive:
- An integrated framework that satisfies both AICPA’s Trust Service Principles and HIPAA’s security rule protections.
- A streamlined process to demonstrate your steadfast commitment to data security.
- Detailed reporting that proves to stakeholders and patients alike that their data is secure and managed with care.
By harmonizing these standards, PBMares helps you demonstrate an exceptional level of commitment to data integrity. Our approach streamlines the audit process, reduces complexity, and provides a clear roadmap to a resilient security posture. With our guidance, your organization can showcase its dedication to safeguarding patient health information and position itself as a leading figure in responsible data stewardship.
Safeguard your organization against data breaches and non-compliance penalties, paving the way to a secure and compliant future to ensure the utmost protection for ePHI.
HITRUST Readiness Assessments: The Path to Certification
As a global authoritative framework, HITRUST CSF is the foundation for healthcare data security. Achieving HITRUST certification demonstrates to your patients, partners, and regulators that your commitment to protecting health information is unwavering. The path to certification can be challenging.
Achieve clarity and a verifiable approach to risk management. With HITRUST readiness assessments, you gain:
- An in-depth analysis of your current security posture against HITRUST CSF requirements.
- A roadmap tailored to your organization’s size and complexity.
- Strategic guidance for addressing gaps and aligning with HITRUST’s prescriptive controls.
- Support throughout the entire HITRUST certification process, from self-assessment to validated assessment (e1, i1, and r2).
HITRUST Assessments: Key Differences
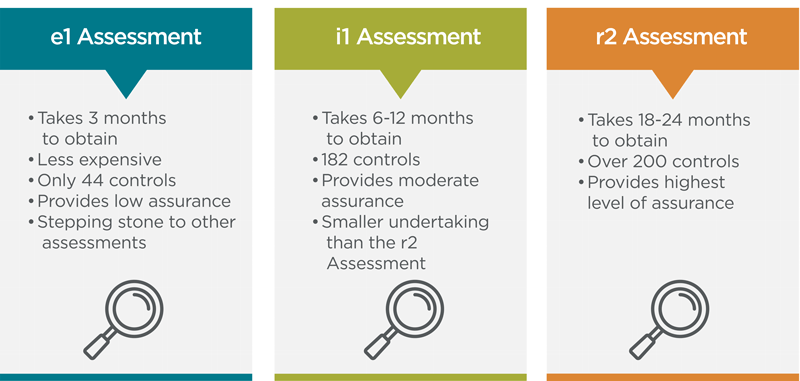
Our team of experts works alongside your staff, demystifying the HITRUST framework and transforming a daunting journey into a seamless stride toward certification.


